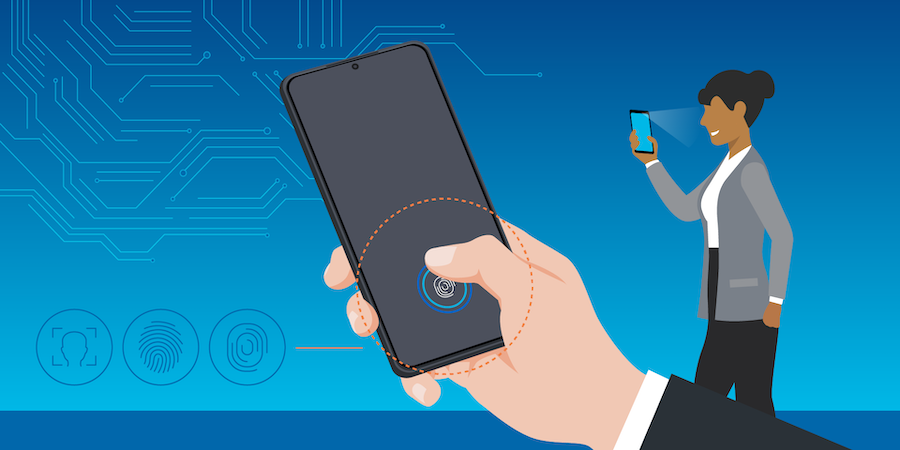
The digital era has surpassed its limit with the security and the development of technologies that can confirm identities. Biometric authentication login is one such method that has developed into the core of security system implementation. These excel in identifying unique characteristics that are unique to the individual and inherited like fingerprints, voice, face, and else while confirming their identity.
Biometrics is stated as the analysis of unique biological characteristics and physiological assets to confirm an individual’s identity. While these can be highly specific and unique to one, there are two types of biometrics systems as below.
-
Physical Biometrics
Physical biometrics perform verification by using special devices such as scanners, sensors, or readers. The individual’s biometric data is stored in the system database, which is later when scanned by the special devices that approve of the authentication and provide access.
Identity verification is much simpler when it comes to modern smartphones as their built-in cameras and video recorders carry out the functions of identity verification when it comes to the owner.
-
Behavioral Biometrics
These are the ones recognizing the individual based on their characteristics. While, these may include multiple dynamics of handwriting, signatures, voice, speech, face, certain gestures, and more. These are termed dynamic biometric authentication login as it is solely based on individuals’ unique behavior.
Different Types of Biometric Authentication for Logins
There are five different types of biometric authentication login identification and verification practices based on the system analysis.
-
Fingerprint Scanning
It is the physical biometrics type, authentication is carried out through a fingerprint scanner and identity is verified. While there is a variety of biometric systems for fingerprint scanning as follows, the user has to just apply their finger to the scanner and wait for the sensor to confirm their identity.
- A fingerprint scanner converts digital code with an optical sensor
- Saves conversion using the linear thermal sensor
- Converts fingerprints with a capacitive authentication sensor
-
Facial and Voice Recognition
Facial recognition has the localization of the human face through the camera, while the facial recognition is a prominent biometric authentication login method for smartphones and most digital devices. The database confirms records and stores them as mathematical codes.
Voice recognition feature inherited by every person as unique to them as fingerprints and faces. The organizations use a biometric authentication login method as voice recognition as it serves high convenience for users and utilizes minimum effort, delivering more efficiency with the system.
-
Handwriting Recognition
Dynamic signature verification applies based on pattern recognition with algorithmic and mathematical analysis that represents every signature. These patterns serve unique to every individual and confirm identities with advanced technological recognition.
-
Palm Recognition
The method of biometric authentication login uses a scanning device and processes image data to compare with the stored records of the individual. The palm prints are counterparts to fingerprints and include similar details enhancing the accuracy of the individual identification.
OmniDefend’s multi-factor authentication, when combined with the robust Biometric authentication login, delivers the highest level of security to organizations that have a huge database and customers to cater to. OmniDefend has biometric support that serves leading-edge fingerprint matching when it comes to the identification of customers from millions of fingerprints in the database in under three seconds.
We also cater to other forms of biometric authentication login apart from fingerprint authentication such as palm scanning, handwriting recognition, and facial and voice recognition. We cater to organizations looking for leveraging their identity management capabilities and elevate the security technology in their businesses.